How to prepare for cyberattacks
An easy-to-digest checklist on the many ways you want protect yourself from a cyberattack before it happens, if it happens, and after it happens.
In the world of cybersecurity, warfare is not just on the battlefield, and security is more than a locked door. It is the realm of schemers and sleuths. We've curated the best resources to make this abstract subject all the more tangible.
Hours of research by our editors, distilled into minutes of clarity.
An easy-to-digest checklist on the many ways you want protect yourself from a cyberattack before it happens, if it happens, and after it happens.
A look at how self-absorbed computer nerds became a powerful force for freedom through time.
Have I Been Pwned allows you to search across multiple data breaches to see if your email address or phone number has been compromised.
A technician bought an old, likely-decommissioned voting machine from 2013 and took it apart to see how a would-be hacker might be able to exploit its vulnerabilities. Get a sense of the needs for secure, up-to-date voting machines with this...

This blog is a preview of the 2022 Crypto Crime Report, offering a summary of ransomware activity in 2021, the most active strains of ransomware, and more (w/ data, charts, and illustrations).
These attacks can manipulate AI behavior by hiding instructions in websites and PDFs that become part of training data. The more companies connect sites, services, and sensitive datasets to AI tools, the greater the chances of exposure to malicious code.
A loose group of thousands of technologists and hackers is attacking Russian services and websites—and scoring significant wins.
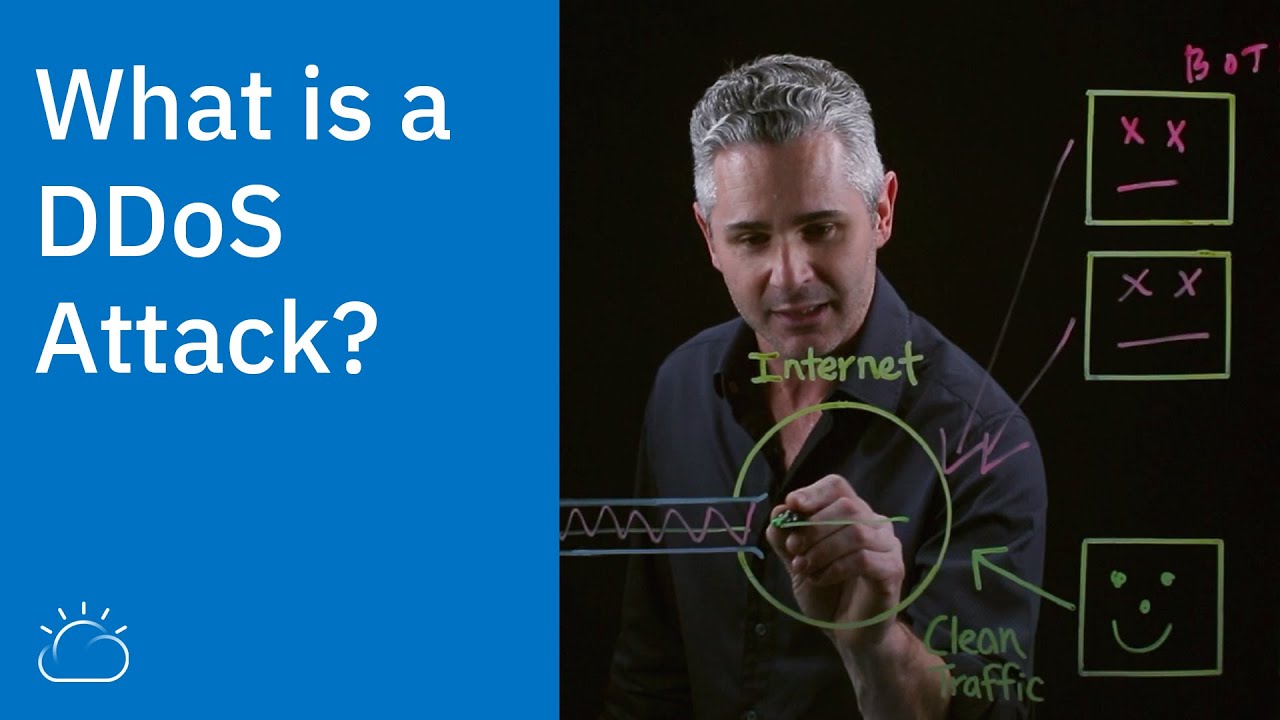
The team at IBM explains the basics of a distributed denial-of-service attack.
Ransomware is malware that locks your keyboard or computer to prevent you from accessing your data until you pay a ransom.
CISA, through the National Risk Management Center (NRMC), is leading risk mitigation efforts by working with government and industry partners to ensure the security and resiliency of 5G technology and infrastructure.